Our Audit Features
Security
Aside from industry standard automatic tools, we do a through line-by-line check of the protocol source code.

Style
Our stylish and easy-to-read project audits aim to provide our clients with the best possible audits.

Speed
Audit reports with recommendations on how to fix the issues and mitigate the risk delivered in 1 day.

Audit Example
Title Page

Summary

Overview
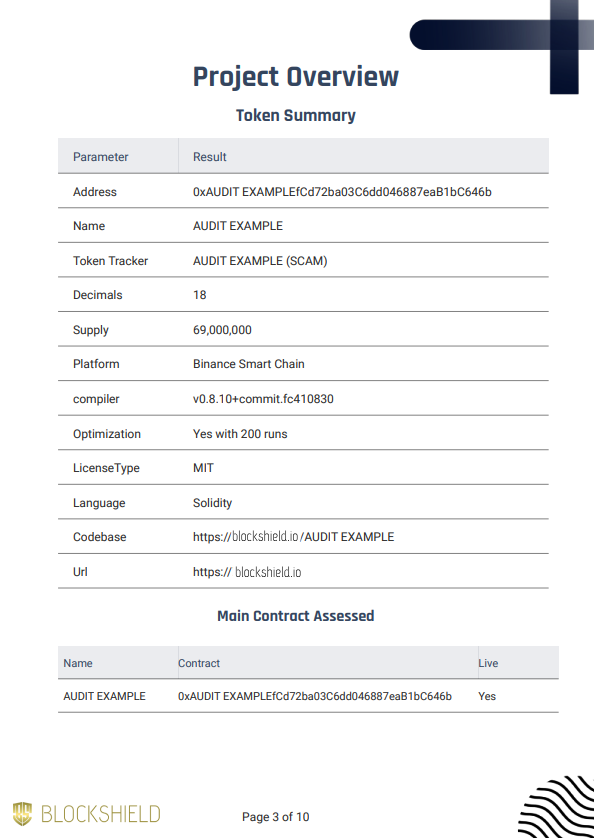
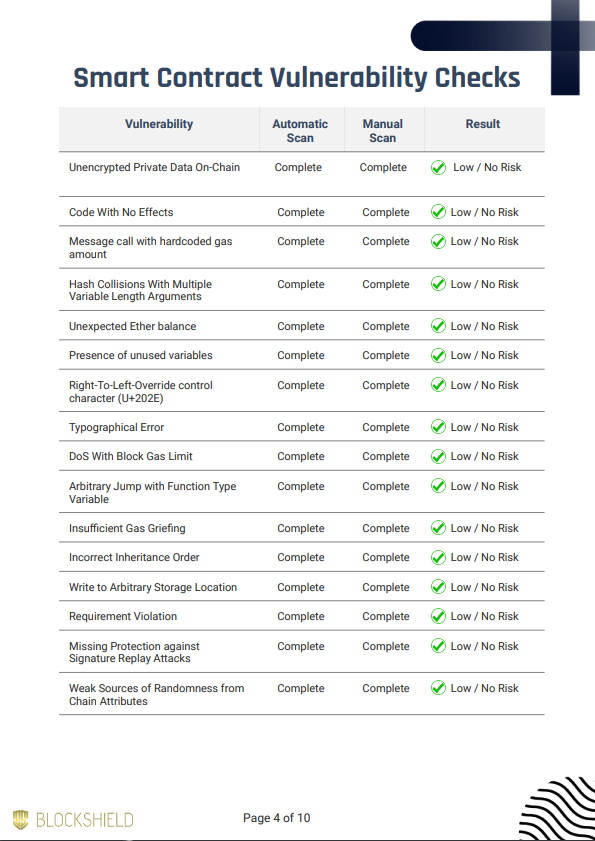
Checks
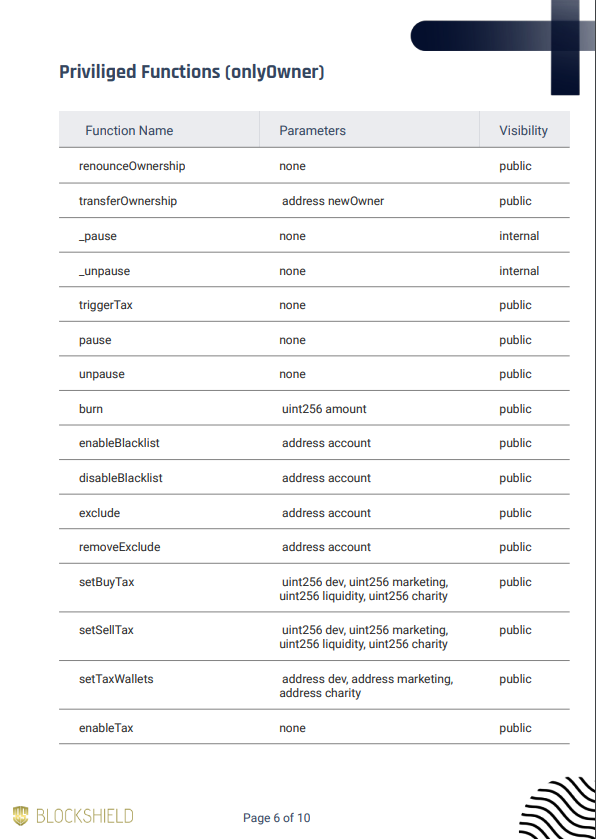
Privileges
And More!
▪ Contract Ownership
▪ Security Findings
▪ Liquidity Info
▪ Token Holders Info
▪ Liquidity Ownership
Make sure to check our past protocol audits to see a full example.


